Revealing that which is concealed. Learning about anything that resembles real freedom. A journey of self-discovery shared with the world. Have no fellowship with the unfruitful works of darkness, but rather reprove them - Ephesians 5-11 Join me and let's follow that high road...
Thursday, December 31, 2015
Intrinsic value vs fiat value
1 silver dollar in 1964 bought 5 gallons of gas. Today, one dollar - in california at least - won't even buy one third (1/3) of a SINGLE GALLON.
But a 1964 Silver Dollar today, STILL BUYS 5 GALLONS OF GAS!
But a 1964 Silver Dollar today, STILL BUYS 5 GALLONS OF GAS!
Wednesday, December 30, 2015
Tuesday, December 29, 2015
Beginning January 1, police in California will confiscate firearms from gun owners thought to be a danger to themselves or others without giving the owner any notice.
This is the result of the implementation of “gun violence restraining orders” (GVROs), which go into effect New Year’s Day.
According to KPCC, GVROs “could be issued without prior knowledge of the person. In other words, a judge could issue the order without ever hearing from the person in question, if there are reasonable grounds to believe the person is a threat based on accounts from the family and police.” And since the order can be issued without the gun owner even being present to defend him or herself, confiscation can commence without any notice to the gun owner once the order is issued.
To be fair, Los Angeles Police Department Assistant Chief Michael Moore does not use the word “confiscate” when talking about confiscating firearms. Rather, Moore says, “The law gives us a vehicle to cause the person to surrender their weapons, to have a time out, if you will.”
KPCC reports that “California law already bans people from possessing guns if they’ve committed a violent crime or were involuntarily committed to a mental health facility.” And now, with GVROs, California law allows judges to bar people from possessing guns even if they have not committed a violent crime or were involuntarily committed. Because of this, Gun Owners of California Executive Director Sam Paredes warns that GVROs “may create a situation where law-abiding gun owners are put in jeopardy.”
http://www.breitbart.com/california/2015/12/29/police-may-confiscate-guns-without-notice-owner-starting-january-1/?utm_source=facebook&utm_medium=social
According to KPCC, GVROs “could be issued without prior knowledge of the person. In other words, a judge could issue the order without ever hearing from the person in question, if there are reasonable grounds to believe the person is a threat based on accounts from the family and police.” And since the order can be issued without the gun owner even being present to defend him or herself, confiscation can commence without any notice to the gun owner once the order is issued.
To be fair, Los Angeles Police Department Assistant Chief Michael Moore does not use the word “confiscate” when talking about confiscating firearms. Rather, Moore says, “The law gives us a vehicle to cause the person to surrender their weapons, to have a time out, if you will.”
KPCC reports that “California law already bans people from possessing guns if they’ve committed a violent crime or were involuntarily committed to a mental health facility.” And now, with GVROs, California law allows judges to bar people from possessing guns even if they have not committed a violent crime or were involuntarily committed. Because of this, Gun Owners of California Executive Director Sam Paredes warns that GVROs “may create a situation where law-abiding gun owners are put in jeopardy.”
http://www.breitbart.com/california/2015/12/29/police-may-confiscate-guns-without-notice-owner-starting-january-1/?utm_source=facebook&utm_medium=social
Monday, December 28, 2015
Sunday, December 27, 2015
Thursday, December 24, 2015
Wednesday, December 23, 2015
Tuesday, December 22, 2015
instead of measuring how regularly you pay your bills, it measures how obediently you follow the party line
As if further proof were needed Orwell’s dystopia is now upon us,
China has now gamified obedience to the State. Though that is every bit
as creepily terrifying as it sounds, citizens may still choose whether
or not they wish to opt-in — that is, until the program becomes
compulsory in 2020. “Going under the innocuous name of ‘Sesame Credit,’ China has created a score for how good a citizen you are,” explains Extra Credits’ video about the program. “The
owners of China’s largest social networks have partnered with the
government to create something akin to the U.S. credit score — but, instead of measuring how regularly you pay your bills, it measures how obediently you follow the party line.”
In the works for years, China’s ‘social credit system’ aims to create a docile, compliant citizenry who are fiscally and morally responsible by employing a game-like format to create self-imposed, group social control. In other words, China gamified peer pressure to control its citizenry; and, though the scheme hasn’t been fully implemented yet, it’s already working — insidiously well.
Zheping Huang, a reporter for Quartz, chronicled his own experience with the social control tool in October, saying that “in the past few weeks I began to notice a mysterious new trend. Numbers were popping up on my social media feeds as my friends and strangers on Weibo [the Chinese equivalent to Twitter] and WeChat began to share their ‘Sesame Credit scores.’ The score is created by Ant Financial, an Alibaba-affiliated company that also runs Alipay, China’s popular third-party payment app with over 350 million users. Ant Financial claims that it evaluates one’s purchasing and spending habits in order to derive a figure that shows how creditworthy someone is.”
However, according to a translation of the “Planning Outline for the Construction of a Social Credit System,” posted online by Oxford University’s China expert, Rogier Creemers, it’s nightmarishly clear the program is far more than just a credit-tracking method. As he described it, “The government wants to build a platform that leverages things like big data, mobile internet, and cloud computing to measure and evaluate different levels of people’s lives in order to create a gamified nudging for people to behave better.”
While Sesame Credit’s roll-out in January has been downplayed by many, the American Civil Liberties Union, among others, urges caution, saying:
James Corbett has been tracking the implementation of Sesame Credit for some time. Introducing the ubiquitous tracking system for a recent episode of the Corbett Report, he mused:
And that, of course, is precisely why gamifying State obedience is so terrifying.
In the works for years, China’s ‘social credit system’ aims to create a docile, compliant citizenry who are fiscally and morally responsible by employing a game-like format to create self-imposed, group social control. In other words, China gamified peer pressure to control its citizenry; and, though the scheme hasn’t been fully implemented yet, it’s already working — insidiously well.
Zheping Huang, a reporter for Quartz, chronicled his own experience with the social control tool in October, saying that “in the past few weeks I began to notice a mysterious new trend. Numbers were popping up on my social media feeds as my friends and strangers on Weibo [the Chinese equivalent to Twitter] and WeChat began to share their ‘Sesame Credit scores.’ The score is created by Ant Financial, an Alibaba-affiliated company that also runs Alipay, China’s popular third-party payment app with over 350 million users. Ant Financial claims that it evaluates one’s purchasing and spending habits in order to derive a figure that shows how creditworthy someone is.”
However, according to a translation of the “Planning Outline for the Construction of a Social Credit System,” posted online by Oxford University’s China expert, Rogier Creemers, it’s nightmarishly clear the program is far more than just a credit-tracking method. As he described it, “The government wants to build a platform that leverages things like big data, mobile internet, and cloud computing to measure and evaluate different levels of people’s lives in order to create a gamified nudging for people to behave better.”
While Sesame Credit’s roll-out in January has been downplayed by many, the American Civil Liberties Union, among others, urges caution, saying:
“The system is run by two companies, Alibaba and Tencent, which run all the social networks in China and therefore have access to a vast amount of data about people’s social ties and activities and what they say. In addition to measuring your ability to pay, as in the United States, the scores serve as a measure of political compliance. Among the things that will hurt a citizen’s score are posting political opinions without prior permission, or posting information that the regime does not like, such as about the Tiananmen Square massacre that the government carried out to hold on to power, or the Shanghai stock market collapse. It will hurt your score not only if you do these things, but if any of your friends do them.” And, in what appears likely the goal of the entire program, added, “Imagine the social pressure against disobedience or dissent that this will create.”Social pressure, of course, can be highly effective given the right circumstances. China seems to have found exactly that in the intricate linking of people’s scores to their contacts, which can be seen publicly by anyone — and then upping the ante through score-based incentives and rewards. Rick Falkvinge pointed out a startling comparison:
“The KGB and the Stasi’s method of preventing dissent from taking hold was to plant so-called agents provocateurs in the general population, people who tried to make people agree with dissent, but who actually were arresting them as soon as they agreed with such dissent. As a result, nobody would dare agree that the government did anything bad, and this was very effective in preventing any large-scale resistance from taking hold. The Chinese way here is much more subtle, but probably more effective still.”Chinese internet specialist at the Swedish Institute of International Affairs, Johan Lagerkvist, said the system is“very ambitious in scope, including scrutinizing individual behavior and what books people read. It’s Amazon’s consumer tracking with an Orwellian political twist.”
As Creemers described to Dutch news outlet, de Volkskrant, “With the help of the latest internet technologies, the government wants to exercise individual surveillance. The Chinese aim […] is clearly an attempt to create a new citizen.”
James Corbett has been tracking the implementation of Sesame Credit for some time. Introducing the ubiquitous tracking system for a recent episode of the Corbett Report, he mused:
“Coming soon to a New World Order near you: social credit! Earn points by behaving like the government wants you to behave! Get penalized if you don’t act like a doubleplusgood citizen! What could be more fun?”Indeed, because mandatory enrollment in Sesame Credit is still a few years away, its true effectiveness won’t be measurable for some time. But even a reporter’s usual wariness appears knocked off-kilter, as Zheping Huang summarized his personal experience, “Even if my crappy credit score doesn’t mean much now, it’s in my best interest I suppose to make sure it doesn’t go too low.”
And that, of course, is precisely why gamifying State obedience is so terrifying.
instead of measuring how regularly you pay your bills, it measures how obediently you follow the party line
As if further proof were needed Orwell’s dystopia is now upon us,
China has now gamified obedience to the State. Though that is every bit
as creepily terrifying as it sounds, citizens may still choose whether
or not they wish to opt-in — that is, until the program becomes
compulsory in 2020. “Going under the innocuous name of ‘Sesame Credit,’ China has created a score for how good a citizen you are,” explains Extra Credits’ video about the program. “The
owners of China’s largest social networks have partnered with the
government to create something akin to the U.S. credit score — but, instead of measuring how regularly you pay your bills, it measures how obediently you follow the party line.”
In the works for years, China’s ‘social credit system’ aims to create a docile, compliant citizenry who are fiscally and morally responsible by employing a game-like format to create self-imposed, group social control. In other words, China gamified peer pressure to control its citizenry; and, though the scheme hasn’t been fully implemented yet, it’s already working — insidiously well.
Zheping Huang, a reporter for Quartz, chronicled his own experience with the social control tool in October, saying that “in the past few weeks I began to notice a mysterious new trend. Numbers were popping up on my social media feeds as my friends and strangers on Weibo [the Chinese equivalent to Twitter] and WeChat began to share their ‘Sesame Credit scores.’ The score is created by Ant Financial, an Alibaba-affiliated company that also runs Alipay, China’s popular third-party payment app with over 350 million users. Ant Financial claims that it evaluates one’s purchasing and spending habits in order to derive a figure that shows how creditworthy someone is.”
However, according to a translation of the “Planning Outline for the Construction of a Social Credit System,” posted online by Oxford University’s China expert, Rogier Creemers, it’s nightmarishly clear the program is far more than just a credit-tracking method. As he described it, “The government wants to build a platform that leverages things like big data, mobile internet, and cloud computing to measure and evaluate different levels of people’s lives in order to create a gamified nudging for people to behave better.”
While Sesame Credit’s roll-out in January has been downplayed by many, the American Civil Liberties Union, among others, urges caution, saying:
James Corbett has been tracking the implementation of Sesame Credit for some time. Introducing the ubiquitous tracking system for a recent episode of the Corbett Report, he mused:
And that, of course, is precisely why gamifying State obedience is so terrifying.
In the works for years, China’s ‘social credit system’ aims to create a docile, compliant citizenry who are fiscally and morally responsible by employing a game-like format to create self-imposed, group social control. In other words, China gamified peer pressure to control its citizenry; and, though the scheme hasn’t been fully implemented yet, it’s already working — insidiously well.
Zheping Huang, a reporter for Quartz, chronicled his own experience with the social control tool in October, saying that “in the past few weeks I began to notice a mysterious new trend. Numbers were popping up on my social media feeds as my friends and strangers on Weibo [the Chinese equivalent to Twitter] and WeChat began to share their ‘Sesame Credit scores.’ The score is created by Ant Financial, an Alibaba-affiliated company that also runs Alipay, China’s popular third-party payment app with over 350 million users. Ant Financial claims that it evaluates one’s purchasing and spending habits in order to derive a figure that shows how creditworthy someone is.”
However, according to a translation of the “Planning Outline for the Construction of a Social Credit System,” posted online by Oxford University’s China expert, Rogier Creemers, it’s nightmarishly clear the program is far more than just a credit-tracking method. As he described it, “The government wants to build a platform that leverages things like big data, mobile internet, and cloud computing to measure and evaluate different levels of people’s lives in order to create a gamified nudging for people to behave better.”
While Sesame Credit’s roll-out in January has been downplayed by many, the American Civil Liberties Union, among others, urges caution, saying:
“The system is run by two companies, Alibaba and Tencent, which run all the social networks in China and therefore have access to a vast amount of data about people’s social ties and activities and what they say. In addition to measuring your ability to pay, as in the United States, the scores serve as a measure of political compliance. Among the things that will hurt a citizen’s score are posting political opinions without prior permission, or posting information that the regime does not like, such as about the Tiananmen Square massacre that the government carried out to hold on to power, or the Shanghai stock market collapse. It will hurt your score not only if you do these things, but if any of your friends do them.” And, in what appears likely the goal of the entire program, added, “Imagine the social pressure against disobedience or dissent that this will create.”Social pressure, of course, can be highly effective given the right circumstances. China seems to have found exactly that in the intricate linking of people’s scores to their contacts, which can be seen publicly by anyone — and then upping the ante through score-based incentives and rewards. Rick Falkvinge pointed out a startling comparison:
“The KGB and the Stasi’s method of preventing dissent from taking hold was to plant so-called agents provocateurs in the general population, people who tried to make people agree with dissent, but who actually were arresting them as soon as they agreed with such dissent. As a result, nobody would dare agree that the government did anything bad, and this was very effective in preventing any large-scale resistance from taking hold. The Chinese way here is much more subtle, but probably more effective still.”Chinese internet specialist at the Swedish Institute of International Affairs, Johan Lagerkvist, said the system is“very ambitious in scope, including scrutinizing individual behavior and what books people read. It’s Amazon’s consumer tracking with an Orwellian political twist.”
As Creemers described to Dutch news outlet, de Volkskrant, “With the help of the latest internet technologies, the government wants to exercise individual surveillance. The Chinese aim […] is clearly an attempt to create a new citizen.”
James Corbett has been tracking the implementation of Sesame Credit for some time. Introducing the ubiquitous tracking system for a recent episode of the Corbett Report, he mused:
“Coming soon to a New World Order near you: social credit! Earn points by behaving like the government wants you to behave! Get penalized if you don’t act like a doubleplusgood citizen! What could be more fun?”Indeed, because mandatory enrollment in Sesame Credit is still a few years away, its true effectiveness won’t be measurable for some time. But even a reporter’s usual wariness appears knocked off-kilter, as Zheping Huang summarized his personal experience, “Even if my crappy credit score doesn’t mean much now, it’s in my best interest I suppose to make sure it doesn’t go too low.”
And that, of course, is precisely why gamifying State obedience is so terrifying.
Monday, December 21, 2015
Exactly How The Government Spies On Your Cell Phone outside of the phone hubs
The release of a secret U.S. government catalog of
cell phone surveillance devices has revealed the names and abilities of
dozens of surveillance tools previously unknown to the public.
The catalog shines a light on well-known devices like the Stingray and
DRT box, as well as new names like Cellbrite, Yellowstone, Blackfin,
Maximus, Stargrazer, and Cyberhawk.

The Intercept reports:
Both the Harris Corp. and the Federal Bureau of Investigations (FBI) require police to sign non-disclosure agreements (NDA) related to the use of the devices. Through these NDAs local police departments have become subordinate to Harris, and even in court cases in front of a judge, are not allowed to speak on the details of their arrangements. Due to this secrecy, very little has been known about how exactly the Stingrays work.
The bit of publicly available information was disclosed through open records requests and lawsuits filed by journalists and researchers. This new catalog provides even more detail about how the devices operate.
We already knew that Stingrays drain the battery of a targeted device, as well as raise signal strength. We also knew that as long as your phone is on, it could be targeted. Some newer details include the fact that the Stingray I and II will not work if the user is “engaged in a call.” Also, the device can gather data from phones within a 200 meter radius. And the next generation Hailstorm device is even capable of cracking encryption on the newer 4G LTE networks.
A number of the devices in the catalog are Digital Receiver Technology (DRT) boxes, also known as dirt boxes, which can be installed in planes for aerial surveillance. DRT was recently purchased by Boeing. We first learned of dirt boxes in late 2014, when the Wall Street Journal revealed a cell phone monitoring program operated by the U.S. Marshals Service, using Cessna planes mounted with Stingrays. AntiMedia has also reported on surveillance planes equipped with thermal imaging technology.
Other devices include:
The Office of the Director of National Intelligence, the FBI, NSA, and U.S. military declined to leave a comment with the Intercept regarding the catalog. Marc Raimondi, a Justice Department spokesperson, told the Intercept that the Department “uses technology in a manner that is consistent with the requirements and protections of the Constitution, including the Fourth Amendment, and applicable statutory authorities.”
The Intercept notes that Raimondi worked for Harris Corp. for six years prior to working for the DOJ.
Secrecy surrounding the use of these devices has been a contentious topic of debate for several years. Truth In Media recently reported that four members of the House Oversight Committee sent letters to 24 federal agencies including the Department of State and the Securities and Exchange Commission, demanding answers regarding policies for using the controversial surveillance technology.
House Oversight Committee Chairman Jason Chaffetz, ranking member Elijah Cummings, and Reps. Will Hurd (R-Texas) and Robin Kelly (D-Ill.), as members of the committee’s IT subcommittee, issued requests for information related to the potential use of stingrays.
Chaffetz also recently introduced the Stingray Privacy Act, which would expand newly established warrant requirements for the Department of Justice and Department of Homeland Security to all federal, state, and local agencies that use the cell-site simulators.
In September, the DHS joined the DOJ by announcing warrant requirements for the use of Stingray equipment, but those rule changes have come under fire for possible loopholes which may allow the continued use of surveillance equipment without a warrant.

The Intercept reports:
“Within the catalogue, the NSA is listed as the vendor of one device, while another was developed for use by the CIA, and another was developed for a special forces requirement. Nearly a third of the entries focus on equipment that seems to have never been described in public before.”As a result, whoever is in possession of the Stingray can figure out who, when, and to where you are calling, the precise location of every device within the range, and with some devices, even capture the content of your conversations.
Anti Media has reported extensively on the Stingray, the brand name of a popular cell-site simulator manufactured by the Harris Corporation. The Electronic Frontier Foundation describes Stingrays as “a brand name of an IMSI (International Mobile Subscriber Identity) Catcher targeted and sold to law enforcement. A Stingray works by masquerading as a cell phone tower – to which your mobile phone sends signals to every 7 to 15 seconds whether you are on a call or not – and tricks your phone into connecting to it.”
Both the Harris Corp. and the Federal Bureau of Investigations (FBI) require police to sign non-disclosure agreements (NDA) related to the use of the devices. Through these NDAs local police departments have become subordinate to Harris, and even in court cases in front of a judge, are not allowed to speak on the details of their arrangements. Due to this secrecy, very little has been known about how exactly the Stingrays work.
The bit of publicly available information was disclosed through open records requests and lawsuits filed by journalists and researchers. This new catalog provides even more detail about how the devices operate.
We already knew that Stingrays drain the battery of a targeted device, as well as raise signal strength. We also knew that as long as your phone is on, it could be targeted. Some newer details include the fact that the Stingray I and II will not work if the user is “engaged in a call.” Also, the device can gather data from phones within a 200 meter radius. And the next generation Hailstorm device is even capable of cracking encryption on the newer 4G LTE networks.
A number of the devices in the catalog are Digital Receiver Technology (DRT) boxes, also known as dirt boxes, which can be installed in planes for aerial surveillance. DRT was recently purchased by Boeing. We first learned of dirt boxes in late 2014, when the Wall Street Journal revealed a cell phone monitoring program operated by the U.S. Marshals Service, using Cessna planes mounted with Stingrays. AntiMedia has also reported on surveillance planes equipped with thermal imaging technology.
Other devices include:
- Cellbrite: “a portable, handheld, field proven forensic system for the quick extraction and analysis of 95% cell phones, smart phones and PDA devices,” capable of extracting “information such as phone book, pictures, video, text messages, and call logs.”
- Kingfish: a Stingray-like device that is “portable enough to be carried around in a backpack.”
- Stargrazer: “an Army system developed to deny, degrade and/or disrupt a targeted adversary’s command and control (C2) system,” which “can jam a handset and capture its metadata at the same time it pinpoints your target’s location. But watch out — the Stargazer may jam all the other phones in the area too — including your own.”
- Cyberhawk: which is capable of gathering “phonebook, names, SMS, media files, text, deleted SMS, calendar items and notes” from 79 cell phones.
The Office of the Director of National Intelligence, the FBI, NSA, and U.S. military declined to leave a comment with the Intercept regarding the catalog. Marc Raimondi, a Justice Department spokesperson, told the Intercept that the Department “uses technology in a manner that is consistent with the requirements and protections of the Constitution, including the Fourth Amendment, and applicable statutory authorities.”
The Intercept notes that Raimondi worked for Harris Corp. for six years prior to working for the DOJ.
Secrecy surrounding the use of these devices has been a contentious topic of debate for several years. Truth In Media recently reported that four members of the House Oversight Committee sent letters to 24 federal agencies including the Department of State and the Securities and Exchange Commission, demanding answers regarding policies for using the controversial surveillance technology.
House Oversight Committee Chairman Jason Chaffetz, ranking member Elijah Cummings, and Reps. Will Hurd (R-Texas) and Robin Kelly (D-Ill.), as members of the committee’s IT subcommittee, issued requests for information related to the potential use of stingrays.
Chaffetz also recently introduced the Stingray Privacy Act, which would expand newly established warrant requirements for the Department of Justice and Department of Homeland Security to all federal, state, and local agencies that use the cell-site simulators.
In September, the DHS joined the DOJ by announcing warrant requirements for the use of Stingray equipment, but those rule changes have come under fire for possible loopholes which may allow the continued use of surveillance equipment without a warrant.
“Because cell-site simulators can collect so much information from innocent people, a simple warrant for their use is not enough,” Jennifer Lynch told the Intercept. “Police officers should be required to limit their use of the device to a short and defined period of time. Officers also need to be clear in the probable cause affidavit supporting the warrant about the device’s capabilities.”At this point, it’s painfully obvious that America is the home of the Police-Surveillance State. Awakened hearts and minds everywhere should continue to educate themselves and their communities about the dangers of these tools. We should also support initiatives to create technology that can defend against the prying eyes and ears of Big Brother. Privacy is a dying notion in a nation of fools determined to be safe rather than liberated. If you give a damn, now is the time to stand up and be heard.
Saturday, December 19, 2015
17 Black Gang Bangers Burned a White Girl Alive… Where Is Obama?
White Life doesn’t mean @#%!. That is the message
THIS White House and the mainstream media wants to make sure it sends loud and clear to the American People.
This is hardly an isolated incident either. There have been quite a few examples of almost medieval anti-white crimes that have flown under the radar during the Obama years that I’ve tried my level best to shine light on with my limited audience so at least SOME people know these crimes ever happened.
Why does it take alternative media to get a story like this out to the American media?
It takes the alternative media because the White House and the “news media” are noticeably absent. It’s unconscionable.
Furthermore, it’s an embarassment to the United States in general, and what our “culture” has devolved into as a whole.
Among the incidents I’m referring to are when a 13 year-old was gang raped by 10 illegal immigrants multiple times at multiple locations, an 88 year-old World War II veteran beaten to death by black teens for no reason, and several other examples provided in the links below.
Mr. Obama, mainstream media, message received.
http://beforeitsnews.com/politics/2015/12/17-black-gang-bangers-burned-a-white-girl-alive-where-is-obama-2765240.html

Thursday, December 17, 2015
MessiahMews Blogs: Anatomy of False-Flag Events
MessiahMews Blogs: Anatomy of False-Flag Events: It's a long article, so click out to read is better... http://www.bibliotecapleyades.net/sociopolitica/sociopol_falseflag33.htm
Money Velocity Is Crashing - Here's Why
The cause of the great depression wasn't the stock market, which recovered immediately in the following months, but rather the CONTRACTION OF THE MONEY SUPPLY AND CREDIT. In short, freezing the velocity of money. And it was intentional.
The inescapable conclusion is that Fed policies have effectively crashed the velocity of money.
That the velocity of money has been crashing while the money supply has been exploding doesn't seem to bother the mainstream pundits. There is always a fancy-footwork explanation of why whatever is crashing no longer matters.
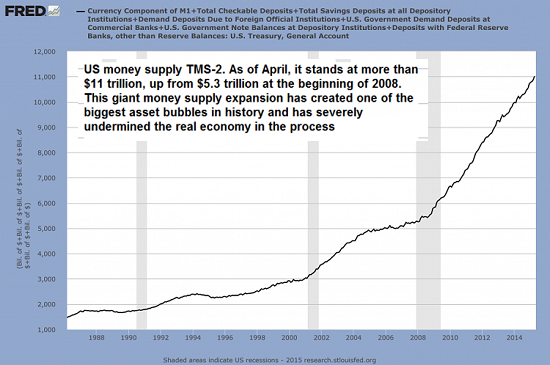
Take a look at these two charts and tell me money velocity doesn't matter. First, here's money supply: notice how money supply leaped from 2001 to 2008 as the Federal Reserve pumped liquidity and credit into the economy, and then how it exploded higher as the Fed went all in after the Global Financial Meltdown.
Now look at a brief history of the velocity of money. There are various measures of money supply and various interpretations of velocity, but let's set those quibbles aside and compare money velocity in the "golden era" of the 1950s/1960s and the stagflationary 1970s to the present era from 2008 to 2015--the era of "growth":
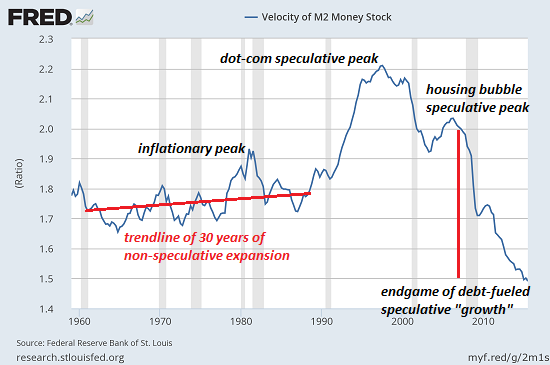
Notice how the velocity of money remained in a mild uptrend during both good times and not so good times. The inflationary peak of 1979-1982 (Treasury yields were 16% and mortgages were 18%) generated a spike, but velocity soon returned to its uptrending channel.
The speculative excesses of the dot-com era pushed velocity to unprecedented heights. Given the extremes in velocity, it is unsurprising that it quickly fell in the dot-com bust.
The Federal Reserve launched an unprecedented expansion of money, credit and liquidity that again pushed velocity up in the speculative frenzy of the housing bubble. But note that despite the vast expansion of money supply, the peak in the velocity of money was considerably lower than the dot-com peak.
Since the collapse of that speculative bubble, the Fed's all-in expansion of money, credit and liquidity has failed to stem the absolutely unprecedented collapse of money velocity. Clearly, expanding money, credit and liquidity no longer generates any velocity.
Rather, the inescapable conclusion is that Fed policies have effectively crashed the velocity of money. How is this possible?
Longtime correspondent Eric A. proposed an insightful explanation. Here is Eric's commentary:
http://www.zerohedge.com/news/2015-12-17/money-velocity-crashing-heres-why
The inescapable conclusion is that Fed policies have effectively crashed the velocity of money.
That the velocity of money has been crashing while the money supply has been exploding doesn't seem to bother the mainstream pundits. There is always a fancy-footwork explanation of why whatever is crashing no longer matters.
Take a look at these two charts and tell me money velocity doesn't matter. First, here's money supply: notice how money supply leaped from 2001 to 2008 as the Federal Reserve pumped liquidity and credit into the economy, and then how it exploded higher as the Fed went all in after the Global Financial Meltdown.

Now look at a brief history of the velocity of money. There are various measures of money supply and various interpretations of velocity, but let's set those quibbles aside and compare money velocity in the "golden era" of the 1950s/1960s and the stagflationary 1970s to the present era from 2008 to 2015--the era of "growth":

Notice how the velocity of money remained in a mild uptrend during both good times and not so good times. The inflationary peak of 1979-1982 (Treasury yields were 16% and mortgages were 18%) generated a spike, but velocity soon returned to its uptrending channel.
The speculative excesses of the dot-com era pushed velocity to unprecedented heights. Given the extremes in velocity, it is unsurprising that it quickly fell in the dot-com bust.
The Federal Reserve launched an unprecedented expansion of money, credit and liquidity that again pushed velocity up in the speculative frenzy of the housing bubble. But note that despite the vast expansion of money supply, the peak in the velocity of money was considerably lower than the dot-com peak.
Since the collapse of that speculative bubble, the Fed's all-in expansion of money, credit and liquidity has failed to stem the absolutely unprecedented collapse of money velocity. Clearly, expanding money, credit and liquidity no longer generates any velocity.
Rather, the inescapable conclusion is that Fed policies have effectively crashed the velocity of money. How is this possible?
Longtime correspondent Eric A. proposed an insightful explanation. Here is Eric's commentary:
"You know how you say that the economy is locked up in fiefdoms, and they're picking winners and losers, as part of colluding the prices? Well this adjustment of prices locks out certain people, like say, the young from housing. So houses don't sell, they stagnate.
But what are we really looking at? Velocity.
Velocity is an indicator that buyers and sellers agree on a price, that the price is "right" and not an outlier. That's why you see a stock move on high volume "confirming" the move, because it means the prices wasn't "right" at the previous level, while more people agree the new price is fair.
If prices are allowed to go where they need to without pressure and manipulation, you will always have velocity, as the most buyers and sellers will always agree at some price. Because this is true, low velocity cannot happen in a free market. Which means the only reason for low velocity (in this or the previous Depressions) is that someone has somehow managed to get an edge that prevents them from selling, from liquidating, at the true price, i.e. the one the buyers will agree to.
This has another corollary, that the measure of velocity on the Fed's own chart is the measure of the level of unnatural price manipulation on the market. We can watch this aggregate indicator of their failure in real time, by the Fed's own hand, and we can know the manipulation is ending when it rises.
So yes, the Fed, the governments, the insiders can manipulate to their heart's content, as they've been doing, but that unnatural pressure goes somewhere. And the pressure diverts into velocity. As we saw in the Great Depression, or the Roman Empire, velocity can stagnate for 10, 20, or 1,000 years until the manipulation ends, property rights are restored, and we have a free market.
History has shown that may be a bargain they're willing to make, but it won't do the rest of us a lot of good."
http://www.zerohedge.com/news/2015-12-17/money-velocity-crashing-heres-why
Wednesday, December 16, 2015
Tuesday, December 15, 2015
Monday, December 14, 2015
Friday, December 11, 2015
Thursday, December 10, 2015
Eugene B. Dinkin is a key to JFK’s assassination
Unfortunately, there are no pictures of Eugene Dinkin, who was an
unfortunate victim of being in the wrong place at the wrong time. At
left is a photo of William K. Harvey, the mad dog alcoholic assassin who
became the CIA’s Knight in Shining Armor. He was told to assassinate
Castro, but the plan soon diverted to JFK.
Dinkin was an army code operator stationed in Mertz, France, when he intercepted a message between a CIA-operative (probably Harvey) who had contacted French mafia in Marseilles to recruit their top assassin (who had the CIA code name QJ/WIN ) for a plot against President Kennedy. Apparently this plot already had the support of some Pentagon brass and a right-wing group in Texas (Murchinson and the Hunt brothers, no doubt). Apparently, some top assassins from a number of secret societies were being recruited. Dinkin made the mistake of telling one of his superiors about this message, as well as his plans to alert the world in order to stop this attempt to kill the President.
Pretty soon, word came down that Dinkin was about to be declared mentally ill, so he went AWOL and escaped into Switzerland, where he attempted to alert the press at a United Nations function. He also sent a letter to Robert Kennedy outlining the plot. Keep in mind, this all happened just days before the assassination, and Dinkin was already telling people the exact date and place the assassination was due to happen.
Of course, Dinkin wasn’t the only insider to blow a whistle before the event. Richard Case Nagell also sent a letter to J. Edgar Hoover outlining the plot. But neither Dinkin’s letter to RFK nor Nagell’s to Hoover have ever been found, and both were likely destroyed. Meanwhile, both Dinkin and Nagell were soon subjected to similar tortures.
Dinkin was soon removed to Walter Reed Army Hospital and worked on for weeks with drugs and electroshock therapy, and by the time he got out, his story has changed considerably. Instead of intercepting a coded message, now he’d predicted the assassination by reading coded messages in the Stars and Stripes? Dick Russell wrote the book on Nagell (The Man Who Knew Too Much) and also happened to get one of the few interviews with Dinkin and he came away with the strong feeling Dinkin had been worked over pretty heavily. Meanwhile, I saw online that his son is trying to raise funds for the definitive book on Dinkin.
In the 1960s, electroshock therapy was being used everywhere, not just by MKULTRA and other brainwashing programs, but also on teenagers who didn’t seem to be fitting in. It was standard treatment for homosexuality, for example. There was no medical science behind electroshock and Ken Kesey was the first to expose the treatment for what it sometimes was: torture. Getting frequent electroshock was sometimes close to a lobotomy and used to subdue patients who weren’t falling into line. It sometimes left victims mentally wrecked, with shattered personalities, which was useful if you were trying to alter that personality, as in what might have happened to Dinkin.
Dinkin was an army code operator stationed in Mertz, France, when he intercepted a message between a CIA-operative (probably Harvey) who had contacted French mafia in Marseilles to recruit their top assassin (who had the CIA code name QJ/WIN ) for a plot against President Kennedy. Apparently this plot already had the support of some Pentagon brass and a right-wing group in Texas (Murchinson and the Hunt brothers, no doubt). Apparently, some top assassins from a number of secret societies were being recruited. Dinkin made the mistake of telling one of his superiors about this message, as well as his plans to alert the world in order to stop this attempt to kill the President.
Pretty soon, word came down that Dinkin was about to be declared mentally ill, so he went AWOL and escaped into Switzerland, where he attempted to alert the press at a United Nations function. He also sent a letter to Robert Kennedy outlining the plot. Keep in mind, this all happened just days before the assassination, and Dinkin was already telling people the exact date and place the assassination was due to happen.
Of course, Dinkin wasn’t the only insider to blow a whistle before the event. Richard Case Nagell also sent a letter to J. Edgar Hoover outlining the plot. But neither Dinkin’s letter to RFK nor Nagell’s to Hoover have ever been found, and both were likely destroyed. Meanwhile, both Dinkin and Nagell were soon subjected to similar tortures.
Dinkin was soon removed to Walter Reed Army Hospital and worked on for weeks with drugs and electroshock therapy, and by the time he got out, his story has changed considerably. Instead of intercepting a coded message, now he’d predicted the assassination by reading coded messages in the Stars and Stripes? Dick Russell wrote the book on Nagell (The Man Who Knew Too Much) and also happened to get one of the few interviews with Dinkin and he came away with the strong feeling Dinkin had been worked over pretty heavily. Meanwhile, I saw online that his son is trying to raise funds for the definitive book on Dinkin.
In the 1960s, electroshock therapy was being used everywhere, not just by MKULTRA and other brainwashing programs, but also on teenagers who didn’t seem to be fitting in. It was standard treatment for homosexuality, for example. There was no medical science behind electroshock and Ken Kesey was the first to expose the treatment for what it sometimes was: torture. Getting frequent electroshock was sometimes close to a lobotomy and used to subdue patients who weren’t falling into line. It sometimes left victims mentally wrecked, with shattered personalities, which was useful if you were trying to alter that personality, as in what might have happened to Dinkin.
Wednesday, December 9, 2015
Tuesday, December 8, 2015
Monday, December 7, 2015
Sunday, December 6, 2015
San Bernardino Attack Eye-Witness: "Three Tall White Men Did It"
And the Patsies were setup, evidence planted, and murdered. These people were OSWALD'd...
A few interesting details have surfaced regarding Wednesday’s mass shooting dubbed ‘terror attack’ which killed 14 and injured 17 others. One of the most interesting comes from an eyewitness.
We now know that ATF investigators recovered police issued firearms from the alleged shooters. This key detail was leaked by 2016 GOP Presidential Candidate Carly Fiorina during a press interview after she had overheard a newsroom report that doesn’t fit the official narrative.
We also know that active shooter drills actually took place near the crime scene just days before and even on the same day of the mass shooting as reported by Mac Slavo.
Additionally details from an eyewitness, who came forth on the day of the shooting, may have been overlooked by investigators and suggest that there were actually ‘three white shooters’ instead of the radicalized husband and wife natural-born killer team portrayed in some mainline reports.
The witness, Sally Abdelmageed, worked at Inland Medical Center where the attack took place and saw it all unfold firsthand. It’s also important to note that Abdelmageed is likely not lying and that this quite possibly might be the most accurate eyewitness account publicized to date. After all how can two shooters, a man and a petite woman, be mistaken for three white military men with athletic builds?
In a phone interview with CBS Abdelmageed explained:
"I heard shots fired and it was from you know an automatic weapon. [...] very unusual. Why would we hear shots? As we looked out the window a second set of shots goes off [...] and we saw a man fall to the floor. Then we just looked and we saw three men dressed in all black, military attire, with vests on they were holding assault rifles. As soon as they opened up the doors to building three [...] one of them [...] started to shoot into the room."When asked what the gunman that shot into the room looked like the eyewitness replied:
"I couldn’t see a face, he had a black hat on […] black cargo pants, the kind with the big puffy pockets on the side [...] long sleeve shirt [...] gloves [...] huge assault rifle [...] six magazines […] I just saw three dressed exactly the same”.“You are certain you saw three men,” the newscaster asked Abdelmageed.
“Yes,” said Abdelmageed.
“It looked like their skin color was white. They look like they were athletic build and they appeared to be tall.”
Friday, December 4, 2015
Subscribe to:
Posts (Atom)


